Wargames
What is the best way to have some fun and learn at the same time? The answer is wargames and CTF.
Wargames (in cybersecurity) are challenges in which the person needs to either exploit or defend vulnerabilities in the system or application. Basically, it makes learning fun.
In this blog, I will be covering one of the popular wargames called Natas from OverTheWire. There are many wargames on the OTW website and you might want to take an attempt solving them before going any further.
This is going to be a very beginner oriented walkthrough. So let’s get started.
Tip! Use Firefox.
General Info
In Web-based wargames, the best approach is to map the app with a Breadth-first technique(mapping the whole surface then going a step deeper) rather than having a Depth-first technique which might end up in a rabbit hole.
Natas: The whole game is divided into 34 levels. Each level can be accessed by username in the format natas<level-number> and a password, found on the previous level which makes the game sequential.
Level 0-1
The foremost thing to do (apart from mapping the app) is to check the source code for any comments or hidden fields.
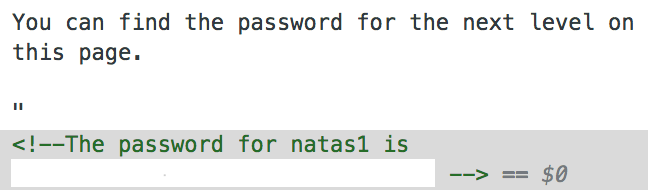
Yay! we got the password for the next level. Finding this was too easy? Wait for the upcoming levels.
Level 1-2
This page says that
You can find the password for the next level on this page, but Right clicking has been blocked!
We have the hint that the password is on the same page but we can’t see the source directly. There are two ways to view source apart from the obvious method.
- Windows: Ctrl + Shift + J or Mac: Cmd + Opt + J will open
Inspect elementfor you, search for the termpassword. - Prepend the site url by
view-source:and press Enter.
Level 2-3
Source code reveals an image in the files directory
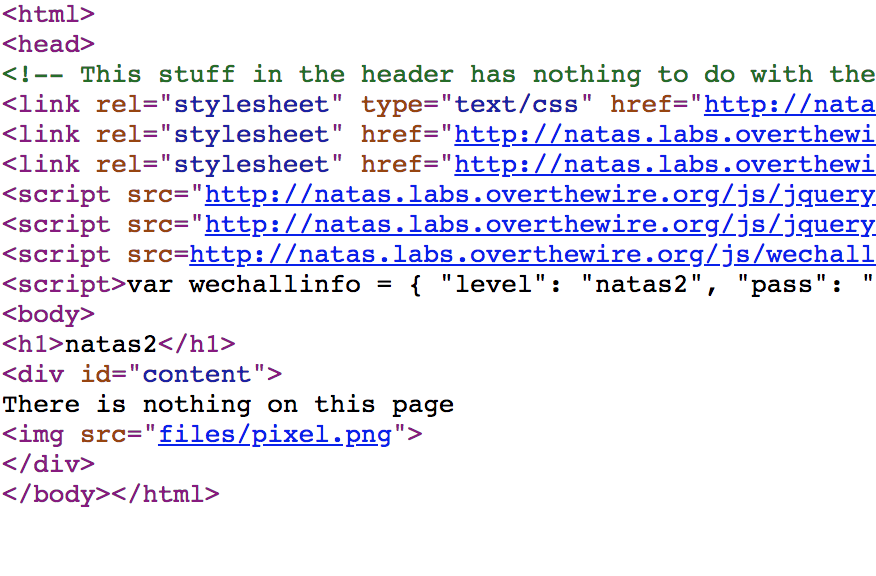
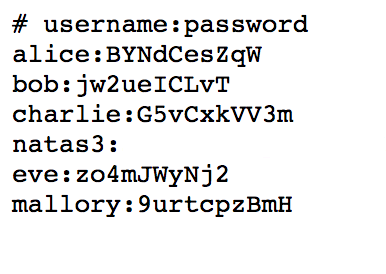
Heading over to the /files/ directory, we will find a users.txt file which reveals the natas3 username and password
Level 3-4
The comment on the source code mentions
No more information leaks!! Not even Google will find it this time…
It’s easy to make an educated guess that it involves the google-bot and hence the robots.txt file. Accessing the file gives us a secret directory named as /s3cr3t/
You will find a users.txt file inside the directory with the password for the next level.
Level 4-5
The page says
Access disallowed. You are visiting from “” while authorized users should come only from “http://natas5.natas.labs.overthewire.org/”
and when clicked on ‘Refresh Page’
Access disallowed. You are visiting from “http://natas4.natas.labs.overthewire.org/index.php” while authorized users should come only from “http://natas5.natas.labs.overthewire.org/”
Using the Referer header in the request, the server knows where we are coming from, to this page.
We can change the header to fool the server. Three ways to do this:
- (Only on Firefox) Head over to the networks tab, right click on the request and resend the request by editing the Referer value using
Edit and Resend - Intercept your request using Burp Suite and edit the value.
curl -H "Referer: http://natas5.natas.labs.overthewire.org/" -H "Authorization: <get-this-through-network-tab>" http://natas4.natas.labs.overthewire.org/[My favourite]
Check response for password
Level 5-6
The page mentions You are not logged in but there hasn’t been any check for authentication Inspecting the GET request with the request and response headers reveal that a cookie is being set. and there hasn’t been any login page, therefore the GET request sent must contain some information.
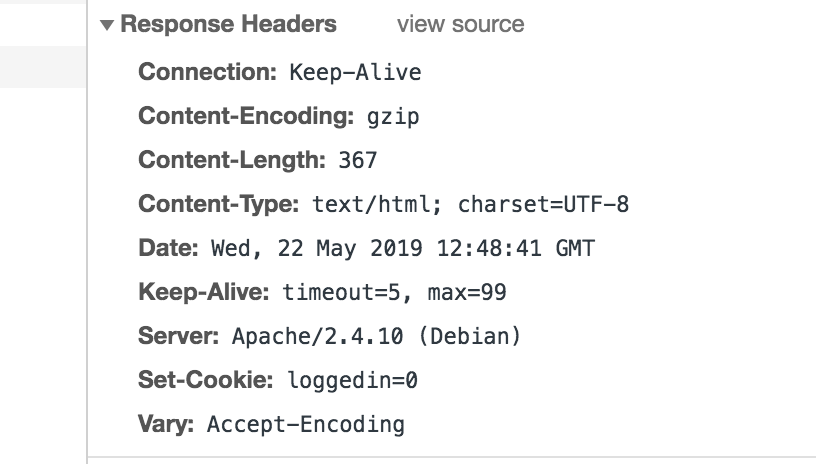
The cookie has a key loggedin with value 0. Changing this to 1 using burp-suite or firefox and sending the modified request will give us the response with the password.
Further Levels
This walkthrough was very beginner oriented and I believe that the levels mentioned will give you a hint of how WebApp Penetration testing looks like. Future walkthroughs would assume that you know basic terminologies and hence will pick up the pace.